Distributed Denial of Service (DDoS) attacks are growing and many organizations are completely unprepared or are have mitigation process that haven’t been battle tested. The effect of a DDoS attack is normally comprised of lost sales & customers, brand damage, and being used as a smoke screen for additional incoming attacks. Organizations with online resources critical to their business are not only at risk of greater losses, but are more likely to be targeted by attackers. It’s for this reason that organizations need to be proactive when dealing with the threat of DDoS.
Types of DDoS Attacks:
- Volumetric
- Reflection and Amplification attacks
- Protocol Attack
- Layer 7 Attack
- Hybrid
Be Proactive
Against the Threat
of DDoS
Can you answer the following questions?
- Where are my DDoS risk areas?
- Is my network capable of handling a DDoS attack?
- Have my current DDoS process and mitigation techniques adequately battle tested?
- What are the limitations of my organization under a DDoS attack?
CCSI DDoS real world simulation or Risk assessment will be able to answer these questions.
We provide tools and expertise to determine your risk posture against DDoS in a proactive manner. At the core of this service is the expertise of a DDoS expert who will be advising clients on their defenses against DDoS. This paired with a proprietary platform that allows CCSI to perform legal DDoS simulations to validate your current defenses. The DDoS simulation platform uses public cloud resources to simulate the same botnet behavior used by real-world attackers under your timeframe and guidance. Unlike a real attack, the simulations are well orchestrated and planned in a manner designed to collect metrics and intelligence while minimizing business risk.
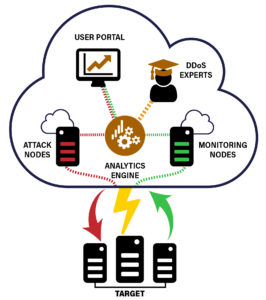
With CCSI’s DDoS simulation and risk assessment we’re taking a proactive approach to dealing with DDoS attacks. Your preparation in dealing with and defending against DDoS attacks will determine how successful you’ll be during an incident. With this offering CCSI is making sure we determine your DDoS risks before attackers find them. We look to test your people, process and technology against controlled attacks under your supervision to validate how prepared you are against attack.

