According to a recent study, a new cyberattack occurs roughly every 39 seconds or 2,244 times a day. A successful attack costs an average of US$3.9 million to identify, eliminate, and recover from. The chance that an attacker will attempt to breach your systems is incredibly high. However, this doesn’t mean you’re helpless.
You can use Endpoint Detection and Response (EDR) to significantly reduce your risks and potential costs. In this article, you’ll learn what EDR is and what kind of threats it can protect you from. You’ll also learn some best practices for implementing EDR to ensure your system is maximally protected.
What Is Endpoint Detection and Response?
EDR solutions are a collection of tools designed to detect and respond to security events occurring on endpoints. Endpoints are the devices or applications on your network that enable access to your internal network. These access points are the gateways that attackers can use to infiltrate your system.
Endpoints include any externally facing device or port, including Internet of Things (IoT) devices, smartphones, laptops, routers, and website portals. Externally facing resources are those which connect to outside networks, such as the Internet.
EDR provides continuous monitoring and greater visibility into events on endpoint devices. It typically works via software agents on your host system or specific endpoint devices. These agents collect event data and send it to a central database for analysis. Since event data is centrally analyzed, you can use EDR to correlate data between multiple endpoints. This enables you to identify suspicious activity that might otherwise be missed.
EDR tools often use forms of machine learning to identify complex, suspicious behavior and to make comparisons against threat intelligence information. In addition to event collection and analysis, these tools often include capabilities for application and device control, encryption, and access control.
Once suspicious activity is identified, you can use EDR tools to automatically respond to issues. These tools can revoke user or application access, isolate infected systems, and track the origin of attack activity.
EDR is particularly useful for identifying and responding to non-traditional threats, including:
- File-less malware—abuses the permissions of legitimate programs and processes to gain access to your systems. Once inside, fileless malware uses system memory to perform malicious tasks such as changing registry values. These attacks do not require files to be downloaded. Instead, this malware relies on scripts and programs that traditional antivirus cannot detect.
- Zero-day exploits—an attack that occurs on the same day that a vulnerability is exposed. There may not be patches available until after the vulnerability is made public, leaving the exploit exposed. Additionally, there are not yet threat signatures for these exploits. This lack makes zero-day attacks undetectable by traditional, signature-based security tools.
- Advanced Persistent Threats (APTs)—attacks carried out over a period of time, often by state-sponsored or organized groups. APTs involve infiltrating your system and remaining undetected. Meanwhile, your systems are mapped, data is exfiltrated, or resources are abused. APTs often use compromised credentials that can be used to bypass security systems and make activity appear legitimate.
EDR Best Practices
EDR solutions can be an effective tool for limiting system access and providing better system visibility. However, these tools alone are not enough to provide complete security. The best practices below can help you implement EDR tools in a way that maximizes your protection.
Take Preventative Action
Whenever possible, you should work to prevent security incidents as opposed to just detecting and responding to attacks. Perform regular security audits to ensure that your configurations are appropriate and that your security policies are being enforced.
Make sure that systems stay up to date with patching and security fixes. Actively watching threat resource threads and vulnerability databases can help ensure you are aware of possible vulnerabilities. Once a vulnerability is known, there is little reason why it should remain exploitable.
Consider implementing threat hunting processes, which involve actively searching for threat activity. Threat hunting can help you identify attacks that bypass your security measures, identify potential system risks, and test the effectiveness of your systems.
Train Your Users
Compromised users and user permissions are two of the most common threats to systems. Phishing schemes, malware, and user error can all grant attackers access to your systems or cause data leakage.
To minimize these risks, you need to make sure that users understand how and why policies and tools are in place. You should also make sure to hold regular threat training and inform users how to identify and alert to possible threats.
When you implement tools and policies, make sure your security measures are as unobtrusive as possible. If security measures are inconvenient or affect productivity, users are likely to work around protections.
Use Complementary Tools
EDR can only protect the borders of your system, not the system in its entirety. You need to combine these tools with other detection and protection tools for full system coverage. This includes patch and vulnerability management solutions, encryption protocols, and user and application access controls.
If possible, combine your security tools into centralized management consoles and dashboards. For example, you can use Security Information and Event Management (SIEM) solutions. SIEMs collect, store, and analyze information across your systems and can alert to identified issues. This centralization makes it easier to monitor and control systems.
You might also consider implementing canary data or deception technologies, like honeypots. Canary data is planted data with no valid purpose. If it is found outside of your systems, it indicates that your data has been compromised. Honeypots are lures for attackers that appear to contain valuable data but in reality, only function as attack alert systems.
Segment Your Network
Network segmentation can help limit attack damage and restrict attacker movement. Segmentation creates boundaries between services or parts of a network using access controls.
Using segmentation, you can restrict the access of endpoints and services to only required resources. You can also layer sensitive data and resources beneath less sensitive layers, making access more difficult for attackers. By layering your segments, you force attackers to pass additional layers of authentication and authorization.
Conclusion
EDR solutions can be a valuable addition to your existing security measures. These tools can identify threats that would otherwise be missed and provide greater insight into your network activity.
Hopefully, this article helped you understand what EDR is and how it can benefit you. By implementing EDR, along with the best practices covered here you can ensure that your systems and data stay as secure as possible.
Author Bio: Gilad David Maayan is a technology writer who has worked with over 150 technology companies including SAP, Samsung NEXT, NetApp and Imperva, producing technical and thought leadership content that elucidates technical solutions for developers and IT leadership. Gilad can be contacted via LinkedIn
Gilad David Maayan is a guest blogger. All opinions are his own.
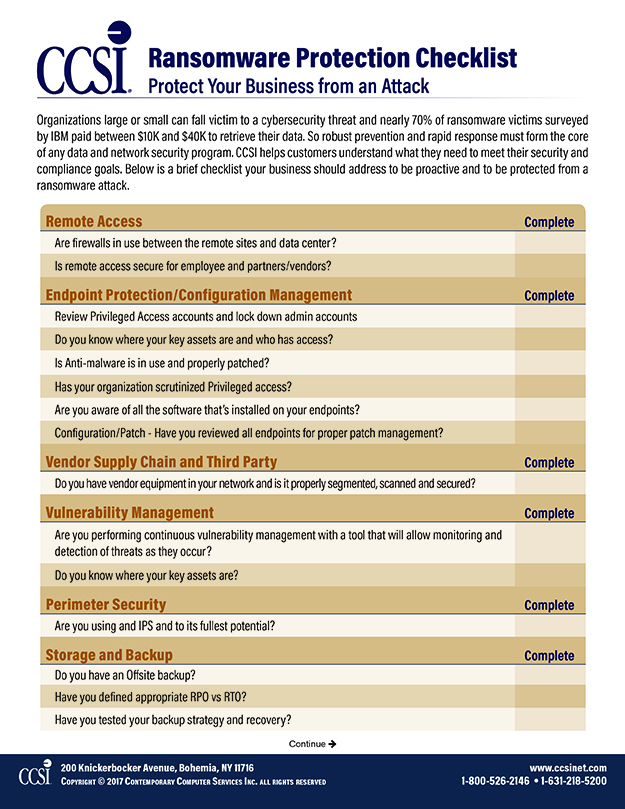
Ransomware Protection Checklist
Ransomware attacks are increasing, but they’re not unstoppable. There is no single layer or control that can be implemented which will completely protect you. Using a layered approach to fight against ransomware and going back-to-basics is the best method to use when defending against attack. Download this checklist for a starting point to protect your organization from the preventable threat of ransomware.