When I started in the technology industry, virtualisation was the hot topic where I was located. Virtualisation enabled organisations to have fewer physical machines, to make use of cloud offerings, and in some cases to reduce the maintenance overhead involved with using software-as-a-service solutions. This is different than containers, which are those beautifully restricted, short-lived dynamic environments that are spun up to complete a sequence of data exchange and related work known as a transaction. The concept of reduced overhead for dynamic environments continues forward.
When creating these massively reduced environments, a technician is able to limit its design to absolutely required services. It’s almost like the principle of least privilege for systems and services i.e. everything required to get the job done but nothing more. This goes to the core of security by design. If done right, the technician has control over exactly what is installed.
What does containerisation bring to the table?
This separation of transactions provides a granular view into each and every transaction and the associated information exchange. In order to be done in the most efficient and resilient way possible, the technician needs to be aware of requirements in relation to both incoming and outgoing exchanges. With this, they can implement robust firewall rules along with the ‘striped down’ version that is a container.
As shown in this diagram below from an article William G Wong wrote in 2016 comparing virtualisation to containerisation, with (a) being virtual machines and (b) containers, we can clearly see the restricted design of containers.
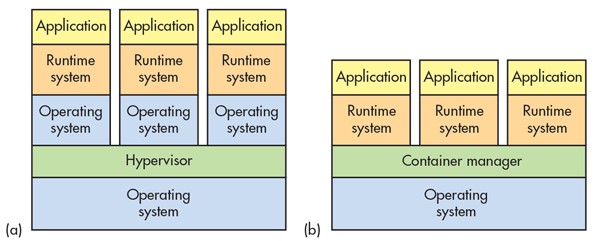
Understanding this provides insight into how containers truly are the bare minimum. As discussed in the article Container Image Security: Beyond Vulnerability Scanning, this separation between application and underlying operating system that containers enable isn’t without it’s security risks. Still, the way containers are designed provides inherent restrictions on the container’s ability to influence the host operating system.
Containers bring that restriction as a benefit. Even if they are compromised, further action is needed to do anything. This increases the likelihood of controls and/or alerts taking notice of anomalous activities and notifying the SOC team.
This level of granular control is exciting from a security perspective. But what other benefits can organizations expect to see?
- Scalability: When I went through network design and management training many moons ago, I found that the number one comment given time after time was ‘always build for the future, make your solutions scalable.’ It is costly to redesign infrastructure. That’s why virtualisation was such a sexy idea to handle capacity influx as required. Containers are there to automatically provide transactions with a home and then die. This is the very meaning of scalable, and it can provide incredible benefits to an organisation.
- Security by Design: As mentioned above, security by design is from the conception of the idea for which security principles are applied. To have any handle on your containerisation lifecycle and effective validation, security must be applied from the beginning. Done right, it can create an extremely beautiful solution.
- Mitigating attacks: Whilst containers are not 100% secure, they do go a long way to reduce the impact of an incident. When one base image is compromised, the ability to quickly identify it and secure this image will affect all further child sessions of it.
- Standardisation: Within the secure development lifecycle, you need to make sure you’re aligning with chosen frameworks and organisational standards by ensuring that all code at a minimum meets these requirements. Containerisation is no exception. Align with the required frameworks, maintain detailed documentation and meet the needs of each phase of deployment.
- Granular view: When done right, tech personnel should have in-depth knowledge and document how their transactions run, what is required and what changes were made and why. They should also identify both a level of acceptable test failure as well as future considerations, and they should have this continuously on hand to investigate any incidents.
- Separation between development, testing, and production: It is rare as a network team member or system administrator that I would have access to replicated environments for testing new configurations and installing updates prior to production. Containerisation requires this to be effectively secured as well as tested for both function and stress. This allows for resilience validation and reduces risk when making changes. It also can provide controls to restrict who has access to make production changes as well as to reduce insider threats and accidental incidents.
Productivity impact of security by design
Whilst it might sound challenging to know these transactions requirements in such depth, the reality is if done from the beginning by only adding in packages/services/features as they’re needed, it brings a sense of clarity to connect the necessary information of each transaction—assuming documentation is maintained, mind you, and appropriate persons are a part of the decision.
This in-depth granular understanding and documentation of transactions means that testing, validation and maintaining constitute the ultimate view of control/configuration/change management. Making sure your container is secure at build time allows for further in-depth review and awareness when validating specific transactions at run-time.
That said, Consider the different security challenges, risks, and attack vectors to ponder within containers. Within the blog, Kubernetes Security 101, the author goes into detail on areas to be reviewed and best practices you can implement to increase the confidence and reduce the inherent risk of your containers.
In 2018, Scott Helme and Ian Thornton-Trump found that actually the ICO website missed this critical piece, resulting in the website running a cryptominer. That might sound outrageous that the ICO didn’t know this was going on, but consider your base images, do any call out to a third-party script or service at run-time? How is the script integrity validated?
Lastly, this article was written with the belief that an organisation and its technicians are fully equipped.
Without the experience, training and a diverse set of skills to approach the container secure lifecycle, this sexy minimalistic approach just becomes a hot vulnerable mess. As noted within this survey of more than 540 IT professionals, 94% of respondents noted that they had experienced a security incident within the last 12 months.
If organisations are looking to decrease this high percentage and effectively implement a containerisation security lifecycle, then the place to start is with the team itself. Not just technical capability, but points of view, passions, experience, and capabilities.
Kubernetes Security – 10 Things You Should Be Doing Webinar
Kubernetes has empowered organizations to build, deploy, and scale applications faster and more efficiently. However, if you are not actively addressing the security challenges in your Kubernetes environments, you are putting your business critical applications at risk. Whether you’re using a cloud provider’s managed Kubernetes service (EKS, AKS, GKE), a Kubernetes distribution (Red Hat OpenShift), or self-managing your clusters, you must protect your containerized applications throughout the application life cycle.
Author Bio: Zoë Rose is a highly regarded hands-on cyber security specialist, who helps her clients better identify and manage their vulnerabilities and embed effective cyber resilience across their organisation. Zoë is a Cisco Champion and certified Splunk Architect, who frequently speaks at international conferences. Recognised in the 50 most influential women in cyber security UK for the past two years, and the PrivSec 200, Zoë is quoted in the media, has presented on National News, has been featured in Vogue Magazine, and was the spokesperson for Nationwide’s Over Sharing campaign that had a reach of 306 million citizens. Zoë is also a regular contributor to Bora.
Zoë is a guest blogger. All opinions are her own.









