We hear about a new major security breach almost every week. Some of them rely on weak keys to do so. In the famous TJ Maxx breach, it is believed the hackers exploited a weak pre-shared key for Wifi. Had they been using WPA2-802.1x the key would have been infinitely stronger. This means the hackers would need to be in the same location for a longer period time and potentially dissuading them from continuing the hack. Even if they stuck around, it would have been obvious to staff that a car was lurking around for too long. Identity management would have helped to enable 802.1x and Radius, which generates unique keys and regenerates them in shorter intervals.
Identity Management
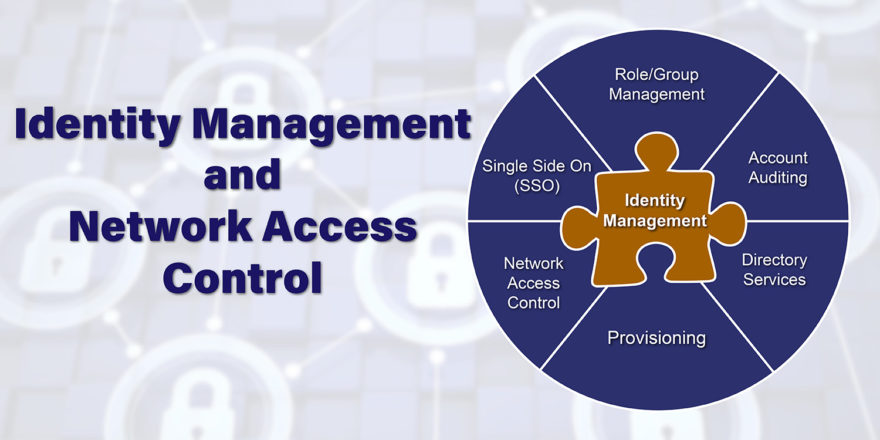
Identity Management is actually a discipline that is a very important to your computer’s security. Essentially, Identity Management is made up of many functions such as: access control, user provisioning, directory services, account auditing, role and group management, single sign-on (SSO), privileged account management, and network access control. Some vendors offer pieces of the Identity Management puzzle, but others like Cisco and Aruba have robust solutions that offer most if not all of these functions. Cisco offers Identity Services Engine (ISE) and Aruba offers ClearPass.
Compliance Growth
Compliance has driven the growth of these suites, as federal regulations govern FIPS, SOX, HIPAA and GLBA, as well as industry standards like PCI DSS have forced companies to account for user access to their systems. These regulations require enterprises to assign unique IDs to each user, be able to report regularly on who has access to systems, and what the users are doing on those systems.
Joel Dubin of searchsecurity.techtarget.com describes the main areas of Identity Management as follows, “There are four pillars to these IAM suites: identity administration, identity infrastructure, access management and auditing.” Identity administration allows for creation and management of user and group roles. Identity infrastructure is the data repository that holds credentials (typically Active Directory, but can be any LDAP-compliant Database). Access Management is the piece of this puzzle that sets up user and corresponding password or even smartcards or biometrics. Last auditing provides a format to report on the accounts, if and how they authenticated and for what they are authorized.
Wikipedia.com defines Network Access Control as follows:
Network Access Control (NAC) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host intrusion prevention, and vulnerability assessment), user or system authentication and network security enforcement.
In the Identity Management realm, NAC serves the purpose of “posturing”. Products like ISE and ClearPass have the ability to execute posture checking against a rule set that checks things like Operating System, Patch level, AntiVirus, etc. Based on the outcome, the endpoint can be placed in a quarantine, granted access or redirected to a URL (to download needed software required for access). Identity management is versatile, because it can be used for access to WLANs (802.11) as well as LANs (802.3). ISE and ClearPass can leverage both RADIUS and TACACS. Regardless of your solution feature rich technology allows powerful identity Management for Windows, Apple, and devices like smart phones. Utilizing Identity Management is really the way of the future. You will probably start to notice that it is in use as you log on to networks at Stores, Coffee shops, and Airports.
Key Tips
Remember that CCSI staffs security specialists certified in many of the industry’s top security vendors. CCSI can custom craft your on-premise security solutions or managed security solution for you. Always look at the details of a public Wifi Hotspot. Make sure it is not wide open and surf carefully. Only use an SSL connection when making electronic transactions involving money or credit cards.

Author Bio:
John Busso is a Senior Network Engineer/Mobility Specialist at CCSI. He has almost 20 years experience providing secure voice and data solutions. John has been a Subject Matter Expert for Enterprise Mobile Solutions such as Guest WiFi and BYOD, providing vision for diverse clients.
John has been an Adjunct Professor and trainer. He holds numerous Industry certifications, including CISSP CWNP, CCNP, ACMP and ITIL. His experience includes working with retail, TNL-Couriers, DC’s and Airports, Healthcare, Education, DOD, Local Government, Financial, Non-Profit-Public WiFi, Entertainment and Hospitality industries. His expertise is in mobility, security, WLAN, WAN, LAN, VoWiFi, RFID, RTLS, WIPS, WIDS, DAS, licensed/unlicensed PTP and PTMP networks.







Security breaches are very common these days. The latest data breach at Yahoo is a very good example of no matter how big the company is, security is always at risk. IAM solution is a very effective platform to manage customers identities in an easy and secure way.